1-5c Review Answers for Security + Guide to Network Security Fundamental
Cyber Security is the merely domain in Information technology which has not faced a recession withal. With need, there is also competition, and to get a chore in Cybersecurity, y'all demand to be one of the best. While having the necessary Cybersecurity skills is half job done, neat the interview is some other affiliate altogether. To help you lot crack the Cyber security interview, nosotros've compiled this listing of meridian Cyber Security interview questions and answers.
Skills matter and so does Certification! Bank check out this Cyber Security Form.
Top Cyber Security Interview Questions
- What is Cryptography?
- What is the difference between Symmetric and Asymmetric encryption?
- What is the difference between IDS and IPS?
- Explain CIA triad.
- How is Encryption different from Hashing?
- What is a Firewall and why is it used?
- What is the difference between VA(Vulnerability Cess) and PT(Penetration Testing)?
- What is a iii-way handshake?
- What are the response codes that can be received from a Web Application?
- What is traceroute? Why is it used?
This Cybersecurity Interview Questions web log is divided into two parts: Office A – Theoretical Cybersecurity Interview Questions and Part B – Scenario Based Cybersecurity Interview Questions .
Let's become started with
Part A-Theoretical Cyber Security Interview Questions
one. What is Cryptography?
Cryptography is the exercise and study of techniques for securing information and communication mainly to protect the data from third parties that the data is not intended for.
2. What is the difference between Symmetric and Asymmetric encryption?
| Basis of Comparison | Symmetric Encryption | Asymmetric Encryption |
| Encryption key | Same key for encryption & decryption | Dissimilar keys for encryption & decryption |
| Operation | Encryption is fast only more vulnerable | Encryption is slow due to high computation |
| Algorithms | DES, 3DES, AES and RC4 | Diffie-Hellman, RSA |
| Purpose | Used for bulk data manual | Often used for securely exchanging secret keys |
3. What is the difference between IDS and IPS?
IDSisIntrusion Detection System and information technology only detects intrusions and the ambassador has to accept care of preventing the intrusion. Whereas, in IPSi.due east.,Intrusion Prevention System, the system detects the intrusion and as well takes actions to foreclose the intrusion.
four. Explain CIA triad.
CIAstands for Confidentiality, Integrity, and Availability. CIAis a model that is designed to guide policies for Information Security. It is ane of the nearly popular models used by organizations.
Confidentiality
The information should be accessible and readable merely to authorized personnel. It should not be accessible past unauthorized personnel. The information should be strongly encrypted just in example someone uses hacking to admission the information then that even if the data is accessed, it is non readable or understandable.
Integrity
Making sure the data has not been modified past an unauthorized entity. Integrity ensures that information is not corrupted or modified by unauthorized personnel. If an authorized individual/arrangement is trying to modify the data and the modification wasn't successful, so the data should be reversed back and should non be corrupted.
Availability
The data should exist available to the user whenever the user requires it. Maintaining of Hardware, upgrading regularly, Data Backups and Recovery, Network Bottlenecks should exist taken intendance of.
Find out our Cyber Security Grooming in Top Cities/Countries
| India | USA | Other Cities/Countries |
| Bangalore | New York | Great britain |
| Hyderabad | Chicago | London |
| Delhi | Atlanta | Canada |
| Chennai | Houston | Toronto |
| Mumbai | Los Angeles | Australia |
| Pune | Boston | UAE |
| Kolkata | Miami | Dubai |
| Ahmedabad | San Francisco | Philippines |
five. How is Encryption unlike from Hashing?
Both Encryption and Hashing are used to convert readable data into an unreadable format. The difference is that the encrypted data can be converted dorsum to original data by the procedure of decryption but the hashed data cannot be converted back to original data.
6. What is a Firewall and why is it used?
A Firewall is a network security system set on the boundaries of the arrangement/network that monitors and controls network traffic. Firewalls are mainly used to protect the system/network from viruses, worms, malware, etc. Firewalls can also exist to prevent remote access and content filtering.
7. What is the departure between VA(Vulnerability Cess) and PT(Penetration Testing)?
Vulnerability Assessment is the process of finding flaws on the target. Here, the organization knows that their arrangement/network has flaws or weaknesses and want to discover these flaws and prioritize the flaws for fixing.
Penetration Testing is the procedure of finding vulnerabilities on the target. In this case, the organization would accept set upward all the security measures they could call back of and would want to examination if there is whatever other style that their system/network can be hacked.
8. What is a three-style handshake?
A 3-way handshake is a method used in a TCP/IP network to create a connection between a host and a client. It's chosen aiii-mode handshakeconsidering it is a three-step method in which the client and server exchanges packets. The three steps are every bit follows:
- The client sends a SYN(Synchronize) packet to the server check if the server is up or has open ports
- The server sends SYN-ACK packet to the customer if it has open up ports
- The client acknowledges this and sends an ACK(Acknowledgment) packet back to the server
ix. What are the response codes that can be received from a Web Application?
1xx – Informational responses
2xx – Success
3xx – Redirection
4xx – Customer-side error
5xx – Server-side fault
Let us now go alee and take a look at some of the other Cybersecurity Interview Questions
10. What is traceroute? Why is it used?
Traceroute is a tool that shows the path of a packet. It lists all the points (mainly routers) that the parcel passes through. This is used more often than not when the packet is not reaching its destination. Traceroute is used to check where the connection stops or breaks to identify the point of failure.
11. What is the difference between HIDS and NIDS?
HIDS(Host IDS) and NIDS(Network IDS) are both Intrusion Detection System and piece of work for the same purpose i.east., to notice the intrusions. The but departure is that the HIDS is set on a particular host/device. It monitors the traffic of a detail device and suspicious arrangement activities. On the other hand, NIDSis gear up on a network. Information technology monitors traffic of all device of the network.
12. What are the steps to set upward a firewall?
Following are the steps to fix up a firewall:
- Username/countersign: modify the default countersign for a firewall device
- Remote administration: Disable the feature of the remote administration
- Port forwarding: Configure appropriate port forwarding for certain applications to work properly, such equally a web server or FTP server
- DHCP server: Installing a firewall on a network with an existing DHCP server will cause conflict unless the firewall's DHCP is disabled
- Logging: To troubleshoot firewall issues or potential attacks, ensure that logging is enabled and understand how to view logs
- Policies: You should have solid security policies in place and brand sure that the firewall is configured to enforce those policies.
13. Explain SSL Encryption
SSL(Secure Sockets Layer)is the industry-standard security engineering creating encrypted connections between Web Server and a Browser. This is used to maintain data privacy and to protect the information in online transactions. The steps for establishing an SSL connection is as follows:
- A browser tries to connect to the webserver secured with SSL
- The browser sends a re-create of its SSL document to the browser
- The browser checks if the SSL document is trustworthy or not. If it is trustworthy, then the browser sends a message to the web server requesting to constitute an encrypted connection
- The web server sends an acknowledgment to showtime an SSL encrypted connection
- SSL encrypted communication takes place betwixt the browser and the spider web server
14. What steps will you take to secure a server?
Secure servers use the Secure Sockets Layer (SSL) protocol for data encryption and decryption to protect information from unauthorized interception.
Here are four unproblematic ways to secure server:
Step ane:Brand sure you have a secure password for your root and ambassador users
Southward tep ii:The next thing you demand to do is make new users on your system. These volition be the users yous utilise to manage the organisation
S tep 3:Remove remote access from the default root/administrator accounts
S tep 4:The next step is to configure your firewall rules for remote access
15. Explain Information Leakage
Data Leakage is an intentional or unintentional manual of data from within the organization to an external unauthorized destination. It is the disclosure of confidential data to an unauthorized entity. Information Leakage can be divided into iii categories based on how it happens:
- Accidental Breach: An entity unintentionally send information to an unauthorized person due to a fault or a blunder
- Intentional Breach: The authorized entity sends data to an unauthorized entity on purpose
- System Hack: Hacking techniques are used to cause information leakage
Data Leakage tin exist prevented by using tools, software, and strategies known as DLP(Information Leakage Prevention) Tools.
16. What are some of the common Cyberattacks?
Following are some common cyber attacks that could adversely affect your organization.
- Malware
- Phishing
- Password Attacks
- DDoS
- Man in the Heart
- Bulldoze-By Downloads
- Malvertising
- Rogue Software

17. What is a Fauna Forcefulness Set on? How can you lot forbid it?
Brute Force is a way of finding out the right credentials by repetitively trying all the permutations and combinations of possible credentials. In most cases, beast forcefulness attacks are automated where the tool/software automatically tries to login with a listing of credentials. There are various ways to prevent Animate being Force attacks. Some of them are:
- Countersign Length: You can set a minimum length for countersign. The lengthier the countersign, the harder information technology is to observe.
- Countersign Complexity: Including unlike formats of characters in the password makes brute force attacks harder. Using alpha-numeric passwords along with special characters, and upper and lower example characters increase the password complexity making information technology hard to exist croaky.
- Limiting Login Attempts: Prepare a limit on login failures. For example, you lot can set the limit on login failures equally 3. So, when there are 3 consecutive login failures, restrict the user from logging in for some time, or send an E-mail or OTP to use to log in the next time. Because animate being force is an automatic process, limiting login attempts will break the brute force process.
18. What is Port Scanning?
Port Scanning is the technique used to identify open up ports and service available on a host. Hackers apply port scanning to find data that tin can be helpful to exploit vulnerabilities. Administrators apply Port Scanning to verify the security policies of the network. Some of the common Port Scanning Techniques are:
- Ping Scan
- TCP One-half-Open
- TCP Connect
- UDP
- Stealth Scanning
Cybersecurity Interview Questions
19. What are the different layers of the OSI model?
An OSI model is a reference model for how applications communicate over a network. The purpose of an OSI reference is to guide vendors and developers so the digital communication products and software programs can interoperate.
Post-obit are the OSI layers: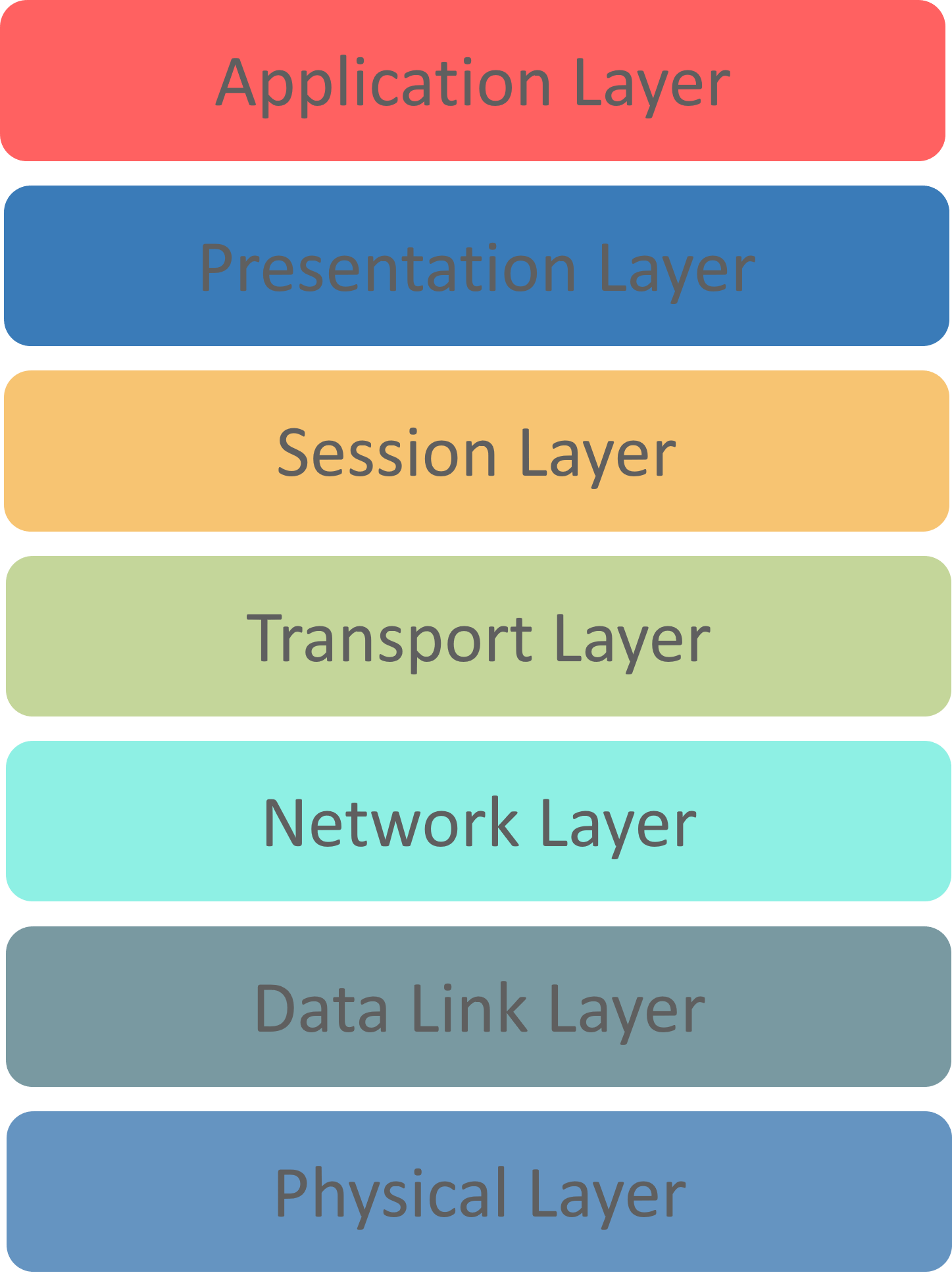
Concrete Layer: Responsible for transmission of digital data from sender to receiver through the communication media,
Data Link Layer: Handles the move of data to and from the physical link. Information technology is also responsible for encoding and decoding of information $.25.
Network Layer: Responsible for packet forwarding and providing routing paths for network communication.
Transport Layer:Responsible for end-to-end advice over the network. It splits the data from the above layer and passes it to the Network Layer and then ensures that all the information has successfully reached at the receiver's stop.
Session Layer: Controls connection betwixt the sender and the receiver. It is responsible for starting, ending, and managing the session and establishing, maintaining and synchronizing interaction betwixt the sender and the receiver.
Presentation Layer:Information technology deals with presenting the data in a proper format and data structure instead of sending raw datagrams or packets.
Awarding Layer: It provides an interface between the application and the network. It focuses on procedure-to-process communication and provides a communication interface.
twenty. What is a VPN?
Almost all Cybersecurity Interview Questions will have this question included. VPN stands forVirtual Individual Network. It is used to create a safe and encrypted connection. When you lot use a VPN, the information from the client is sent to a bespeak in the VPN where it is encrypted and then sent through the internet to another betoken. At this signal, the data is decrypted and sent to the server. When the server sends a response, the response is sent to a betoken in the VPN where it is encrypted and this encrypted data is sent to another signal in the VPN where it is decrypted. And finally, the decrypted data is sent to the client. The whole indicate of using a VPN is to ensure encrypted data transfer.
21. What practice you lot understand by Gamble, Vulnerability & Threat in a network?
Threat: Someone with the potential to harm a system or an organization
Vulnerability: Weakness in a system that tin be exploited by a potential hacker
Risk: Potential for loss or harm when threat exploits a vulnerability
22. How can identity theft be prevented?
Here'south what y'all can practise to prevent identity theft:
-
- Ensure strong and unique password
- Avoid sharing confidential information online, especially on social media
- Shop from known and trusted websites
- Use the latest version of the browsers
- Install advanced malware and spyware tools
- Utilise specialized security solutions confronting financial data
- Ever update your organization and the software
- Protect your SSN (Social Security Number)
23. What are blackness hat, white hat and grey hat hackers?
Black hat hackers are known for having vast noesis almost breaking into computer networks. They tin can write malware which can be used to gain admission to these systems. This type of hackers misuse their skills to steal information or use the hacked system for malicious purpose.
White hat hackers utilize their powers for skillful deeds and so they are also called Ethical Hackers. These are mostly hired by companies as a security specialist that attempts to observe and set up vulnerabilities and security holes in the systems. They use their skills to assist make the security better.
Anonymity is only a simple thing in Ethical Hacking & CyberSecurity. If you are interested in this domain, cheque Edureka's CompTIA Security+ Certification Training.
Grey hat hackers are an amalgamation of a white hat and black hat hacker. They expect for organization vulnerabilities without the owner'south permission. If they find whatever vulnerabilities, they report it to the owner. Unlike Blackness hat hackers, they do not exploit the vulnerabilities constitute.
24. How often should you perform Patch management?
Patch management should be done as soon as it is released. For windows, once the patch is released information technology should be applied to all machines, not afterwards than one calendar month. Aforementioned goes for network devices, patch it every bit soon as it is released. Proper patch direction should exist followed.
25. How would you reset a password-protected BIOS configuration?
Since BIOS is a pre-boot system information technology has its own storage mechanism for settings and preferences. A simple way to reset is past popping out the CMOS battery so that the memory storing the settings lose its power supply and as a consequence, it will lose its setting.
26. Explicate MITM assault and how to prevent it?
A MITM(Man-in-the-Center)attack is a type of attack where the hacker places himself in between the communication of two parties and steal the information. Suppose there are two partiesAandB having a communication. And then the hacker joins this communication. He impersonates as partyB toAand impersonates as partyAin front of B.The data from both the parties are sent to the hacker and the hacker redirects the data to the destination party subsequently stealing the data required. While the two parties think that they are communicating with each other, in reality, they are communicating with the hacker.
You can prevent MITM attack by using the following practices:
- Employ VPN
- Use strong WEP/WPA encryption
- Use Intrusion Detection Systems
- Force HTTPS
- Public Key Pair Based Hallmark
27. Explicate DDOS attack and how to prevent information technology?
This again is an important Cybersecurity Interview Question. A DDOS(Distributed Denial of Service) assault is a cyberattack that causes the servers to decline to provide services to 18-carat clients. DDOS attack can be classified into two types:
- Flooding attacks: In this type, the hacker sends a huge amount of traffic to the server which the server can not handle. And hence, the server stops functioning. This blazon of attack is normally executed by using automatic programs that continuously transport packets to the server.
- Crash attacks:In this type, the hackers exploit a bug on the server resulting in the system to crash and hence the server is not able to provide service to the clients.
You can prevent DDOS attacks by using the following practices:
- Use Anti-DDOS services
- Configure Firewalls and Routers
- Apply Front-Terminate Hardware
- Apply Load Balancing
- Handle Spikes in Traffic
Cybersecurity Interview Questions
28. Explain XSS attack and how to prevent it?
XSS(Cross-Site Scripting)is a cyberattack that enables hackers to inject malicious client-side scripts into web pages. XSS can be used to hijack sessions and steal cookies, modify DOM, remote code execution, crash the server etc.
You can prevent XSS attacks by using the following practices:
- Validate user inputs
- Sanitize user inputs
- Encode special characters
- Apply Anti-XSS services/tools
- Use XSS HTML Filter
29. What is an ARP and how does it work?
Address Resolution Protocol (ARP)is a protocol for mapping an Internet Protocol address (IP address) to a physical machine address that is recognized in the local network.
When an incoming packet destined for a host machine on a item local area network arrives at a gateway, the gateway asks the ARP program to notice a physical host or MAC accost that matches the IP accost.
The ARP program looks in the ARP enshroud and, if it finds the address, provides it so that the packet can be converted to the right parcel length and format and sent to the auto.
If no entry is institute for the IP accost, ARP broadcasts a request packet in a special format to all the machines on the LAN to see if one machine knows that it has that IP address associated with it.
30. What is port blocking within LAN?
Restricting the users from accessing a gear up of services within the local area network is chosen port blocking.
Stopping the source to not to admission the destination node via ports. Every bit the application works on the ports, so ports are blocked to restricts the access filling upwardly the security holes in the network infrastructure.
31. What protocols fall nether TCP/IP net layer?
| TCP/IP | TCP/IP Protocol Examples |
| Application | NFS, NIS+, DNS, telnet, ftp, rlogin, rsh, rcp, RIP, RDISC, SNMP and others |
| Ship | TCP, UDP |
| Internet | IP, ARP, ICMP |
| Data Link | PPP, IEEE 802.2 |
| Physical Network | Ethernet (IEEE 802.3) Token ring, RS-232, others |
32. What is a Botnet?
A Botnet is a number of devices connected to the internet where each device has one or more bots running on it. The bots on the devices and malicious scripts used to hack a victim. Botnets can exist used to steal data, ship spams and execute a DDOS attack.
33. What are salted hashes?
Salt is a random data. When a properly protected password system receives a new password, it creates a hash value of that password, a random table salt value, and then the combined value is stored in its database. This helps to defend against dictionary attacks and known hash attacks.
Example: If someone uses the same password on 2 dissimilar systems and they are being used using the aforementioned hashing algorithm, the hash value would be same, notwithstanding, if even 1 of the system uses salt with the hashes, the value will exist different.
34. Explain SSL and TLS
SSL is meant to verify the sender'southward identity simply it doesn't search for anything more than that. SSL can help you track the person y'all are talking to simply that tin also exist tricked at times.
TLS is also an identification tool just similar SSL, merely it offers improve security features. It provides additional protection to the data and hence SSL and TLS are oftentimes used together for amend protection.
35. What is information protection in transit vs information protection at rest?
| Information Protection in transit | Data protection at balance |
| When data is going from server to client | When information but exists in its database or on its hard bulldoze |
| Effective Information protection measures for in-transit data are disquisitional every bit data is less secure when in motion | Data at rest is sometimes considered to exist less vulnerable than data in transit |
36. What is 2FA and how can it be implemented for public websites?
An extra layer of security that is known as "multi-gene authentication".
Requires not only a countersign and username but also something that but, and only, that user has on them, i.due east. a slice of data only they should know or take immediately to hand – such as a physical token.
Authenticator apps replace the need to obtain a verification code via text, voice telephone call or electronic mail.
37. What is Cognitive Cybersecurity?
Cerebral Cybersecurity is an application of AI technologies patterned on human thought processes to detect threats and protect physical and digital systems.
Cocky-learning security systems use data mining, blueprint recognition, and natural language processing to simulate the human brain, albeit in a loftier-powered computer model.
38. What is the difference between VPN and VLAN?
| VPN | VLAN |
| Helps to group workstations that are non within the same locations into the same broadcast domain | Related to remote access to the network of a company |
| Ways to logically segregate networks without physically segregating them with various switches | Used to connect two points in a secured and encrypted tunnel |
| Saves the data from prying eyes while in transit and no one on the net can capture the packets and read the information | Does non involve any encryption technique but it is merely used to slice up your logical network into dissimilar sections for the purpose of direction and security |
39. Explicate Phishing and how to prevent it?
Phishingis a Cyberattack in which a hacker disguises equally a trustworthy person or business and endeavor to steal sensitive financial or personal data through fraudulent email or instant message.
You tin forbid Phishing attacks by using the following practices:
- Don't enter sensitive data in the webpages that you don't trust
- Verify the site's security
- Use Firewalls
- Apply AntiVirus Software that has Internet Security
- Use Anti-Phishing Toolbar
forty. Explain SQL Injection and how to forbid it?
SQL Injection (SQLi) is a lawmaking injection attack where an assaulter manipulates the data beingness sent to the server to execute malicious SQL statements to control a web application'southward database server, thereby accessing, modifying and deleting unauthorized data. This attack is mainly used to have over database servers.
Y'all can prevent SQL Injection attacks by using the following practices:
- Utilise prepared statements
- Use Stored Procedures
- Validate user input
This brings us to the end of Theory Based Cybersecurity Interview Questions
Desire to upskill yourself to get alee in your career? Check out this video
Meridian 10 Technologies to Learn in 2022 | Edureka
Office B – Scenario Based Cybersec urity Interview Questions
ane. Hither'southward a state of affairs- You receive the post-obit electronic mail from the help desk-bound:
Dear XYZ Electronic mail user,
To create space for more users we're deleting all inactive email accounts. Here's what you lot accept to transport to save your business relationship from getting deleted:
- Name (kickoff and terminal):
- Email Login:
- Password:
- Appointment of birth:
- Alternate email
If we don't receive the to a higher place information from you by the end of the week, your e-mail account will be terminated.
If you lot're a user what do yous do? Justify your answer.
This electronic mail is a classic example of "phishing" – trying to play a trick on yous into "biting". The justification is the generalized way of addressing the receiver which is used in mass spam emails.
Above that, a corporate company will never enquire for personal details on post.
They want your data. Don't reply to email, instant messages (IM), texts, phone calls, etc., asking yous for your password or other individual information.
You should never disclose your countersign to anyone, even if they say they work for UCSC, ITS, or other campus organizations.
2. A friend of yours sends an e-bill of fare to your mail. Yous have to click on the attachment to get the card.
What practise you do? Justify your answer
In that location are iv risks hither:
- Some attachments contain viruses or other malicious programs, and then just in general, it'due south risky to open unknown or unsolicited attachments.
- Besides, in some cases just clicking on a malicious link can infect a computer, so unless you are certain a link is safe, don't click on information technology.
- Email addresses can be faked, and then just because the email says information technology is from someone you know, you can't exist sure of this without checking with the person.
- Finally, some websites and links wait legitimate, just they're really hoaxes designed to steal your data.
iii. Ane of the staff members in XYZ subscribes to many free magazines. Now, to actuate her subscriptions one of the magazines asked for her month of birth, second asked for her year of birth, the other one asked for her maiden name.
What do you infer from this situation? Justify.
All iii newsletters probably accept the same parent company or are distributed through the same service. The parent company or service tin can combine individual pieces of seemingly-harmless information and use or sell it for identity theft
Information technology is even possible that there is a fourth newsletter that asks for a twenty-four hour period of nascence as ane of the activation questions
Oft questions about personal information are optional. In addition to being suspicious nearly situations like the one described here, never provide personal information when information technology is not legitimately necessary, or to people or companies, you don't personally know.
4. In our computing labs, print billing is often tied to the user'due south login. Sometimes people call to complain nearly bills for printing they never did only to notice out that the bills are, indeed, correct.
What do yous infer from this situation? Justify.
Sometimes they realize they loaned their account to a friend who couldn't remember his/her password, and the friend did the printing. Thus the charges. Information technology'due south besides possible that somebody came in behind them and used their account
This is an outcome with shared or public computers in general. If yous don't log out of the computer properly when yous leave, someone else can come in behind you and retrieve what you were doing, utilise your accounts, etc. E'er log out of all accounts, quit programs, and close browser windows before you walk away.
5. There is this case that happened in my calculator lab. A friend of mine used their yahoo account at a estimator lab on campus. She ensured that her account was not left open before she left the lab. Someone came later on her and used the same browser to re-access her business relationship. and they started sending emails from it.
What do you think might be going on hither?
The first person probably didn't log out of her account, so the new person could just become to history and access her account.
Another possibility is that she did log out, merely didn't articulate her spider web enshroud. (This is done through the browser bill of fare to clear pages that the browser has saved for future utilize.)
half dozen. Two dissimilar offices on campus are working to straighten out an error in an employee's bank business relationship due to a directly deposit error.
Office #i emails the right account and eolith information to part #2, which promptly fixes the problem.
The employee confirms with the bank that everything has, indeed, been straightened out.
What is wrong here?
Account and eolith data is sensitive information that could be used for identity theft. Sending this or whatever kind of sensitive information by electronic mail is very risky considering email is typically not private or secure. Anyone who knows how can access information technology anywhere along its route.
As an alternative, the ii offices could accept chosen each other or worked with ITS to send the information a more secure fashion.
7. The mouse on your figurer screen starts to move around on its own and click on things on your desktop. What practice you do?
a) Call your co-workers over so they can see
b) Disconnect your computer from the network
c) Unplug your mouse
d) Tell your supervisor
e) Turn your reckoner off
f) Run anti-virus
g) All of the above
Select all the options that apply.
Right answer is B & D.
This is definitely suspicious. Immediately study the problem to your supervisor and the ITS Support Centre: itrequest.ucsc.edu, 459-HELP (4357), help@ucsc.edu or Kerr Hall room 54, M-F 8AM-5PM
Likewise, since it seems possible that someone is decision-making the calculator remotely, information technology is best if you can disconnect the reckoner from the network (and turn off wireless if you take information technology) until help arrives. If possible, don't turn off the calculator.
8. Below is a listing of passwords pulled out a database.
A. @#$)*&^%
B. akHGksmLN
C.UcSc4Evr!
D.Password1
Which of the post-obit passwords meets UCSC's password requirements?
Respond is UcSc4Evr!
This is the only choice that meets all of the following UCSC requirements:
At least 8 characters in length
Contains at least 3 of the following four types of characters: lower case letters, upper case messages, numbers, special characters
Not a word preceded or followed by a digit
9. Yous receive an email from your banking concern telling you there is a problem with your account. The email provides instructions and a link and so you tin log into your account and set up the problem.
What should you exercise?
Delete the e-mail. Better nevertheless, use the web client (e.g. gmail, yahoo mail, etc.) and report information technology as spam or phishing, then delete it.
Any unsolicited email or phone phone call request you to enter your account information, disembalm your password, financial account data, social security number, or other personal or private data is suspicious – even if it appears to exist from a company y'all are familiar with. Always contact the sender using a method you know is legitimate to verify that the message is from them.
10. A while dorsum, the IT folks got a number of complaints that i of our campus computers was sending out Viagra spam. They checked it out, and the reports were true: a hacker had installed a plan on the computer that fabricated it automatically send out tons of spam electronic mail without the estimator possessor's noesis.
How do you think the hacker got into the reckoner to set this upward?
This was actually the issue of a hacked countersign. Using passwords that can't be easily guessed, and protecting your passwords by not sharing them or writing them down can help to prevent this. Passwords should exist at to the lowest degree 8 characters in length and use a mixture of upper and lower case messages, numbers, and symbols.
Even though in this case it was a hacked password, other things that could mayhap lead to this are:
- Out of date patches/updates
- No anti-virus software or out of date anti-virus software
I hope these Cybersecurity Interview Questions will aid you perform well in your interview. To go proficient join our Cyber Security Masters Programme today. And I wish you all the best!
If you wish to acquire more and build a colorful career, then check out our Cyber Security Course in Republic of india which comes with teacher-led live training and real-life project experience. This training will help you lot sympathize Linux Administration in-depth and help you accomplish mastery over the bailiwick.
You can also have a look at our newly launched course on CompTIA Security+ Certification which is a start-of-a-kind official partnership between Edureka & CompTIA Security+. It offers you lot a chance to earn a global certification that focuses on core cybersecurity skills which are indispensable for security and network administrators.
Besides, learn Cybersecurity the right way with Edureka's POST GRADUATE PROGRAM withNIT Rourkela and defend the world'due south biggest companies from phishers, hackers and cyber attacks.
Got a question for us? Please post it on Edureka Community and we will get back to y'all.
Source: https://www.edureka.co/blog/interview-questions/cybersecurity-interview-questions/
0 Response to "1-5c Review Answers for Security + Guide to Network Security Fundamental"
Post a Comment